What do alerts from a bank’s SOC (security operations center) have in common with alerts from its AML and sanctions screening systems? One key thing: Agentic AI can transform those alerts from a massive labor burden to a non-issue in a matter of months, even weeks. Not only are the proven AI efficiency and efficacy gains in each area impressive, IT leaders can follow the same playbook for each, making transformation predictable and repeatable. We explain here:
Alerts without resolutions
For nearly three decades, financial crime compliance teams have employed transaction screening tools to identify potential risks of money laundering, use of the bank by sanctioned parties and politically exposed people (PEPs), criminals, terrorists, and numerous other BSA/AML infractions. These systems generate hundreds, even thousands of alerts per day, depending on the size of the bank. The sheer volume of alerts overwhelms the typical FCC operations team, as Level 1 analysts simply lack the time to review them, much less make decisions around the one percent of alerts that truly reveal risk.
Mention this challenge of “too many alerts, too few FCC analysts” to a CISO in charge of the bank’s SOC, and you will hear, “Oh yes, we face the same problem with security alert volumes coming from our SIEM tool.”
Prior to Agentic AI, FCC and SOC teams attempted to overcome their crush of alerts in different ways. On the FCC side, leaders maintained steady L1 analyst staffing levels, then expanded resources by outsourcing or hiring temporary labor during times of alert volume surges, such as immediately following the 2022 Russia invasion of Ukraine. On the SOC side, CISOs implemented SOAR systems (Security, Orchestration, Automation and Response) that promised to automatically investigate SIEM alerts and resolve them before human analysts had to get involved.
Unfortunately for both FCC and SOC analyst teams, none of the approaches worked effectively or efficiently, and as of today, most CIOs continue to deal with the problems brought on by massive volumes of unresolved alerts, which include:
- Alert fatigue
- Low employee morale
- Inability to pinpoint true threats among thousands of false positives
- High cost to stay secure and/or in compliance with regulations
The costs to implement SIEM and monitoring systems have been high, deserving of more value. The global transaction monitoring market in the banking industry was valued at approximately USD 18 billion in 2024 and is projected to reach USD 50.71 billion by 2032, according to Fortune Business Insights. Meanwhile, the combined SIEM and SOAR market was valued at USD 5.5 billion and projected to reach nearly USD 20 billion by 2030, according to data from Grand View Research and MARKETSandMARKETS.
Core systems have AI, but not AI Agents
While it is true that SIEM, SOAR, and FCC monitoring systems incorporate AI capabilities, they are not the type that can take an alert, gather contextual data around it, analyze it, make a decision, write up its reasoning, and either file or escalate the alert to a human. Instead, these systems use LLMs (large language models) and GenAI (generative AI) to perform base screening and provide some narratives. What they lack are true AI Agents that can do the work of humans based on years’ worth of prior knowledge baked into them, and make decisions just like L1 analysts do.
AI Agents (for both SOCs and FCC compliance ops) perform the entire end-to-end alert review process just like your best human analysts. Yet, they never tire as they gobble up and disposition thousands of false positive alerts, escalating the few true positives to their human teammates who perform the complex investigations required for true risk mitigation.
AI Agents in action
To demonstrate how AI Agents can deliver on the promise of your existing systems, here is how the WorkFusion AI Agent named “Evan” for adverse media monitoring works:
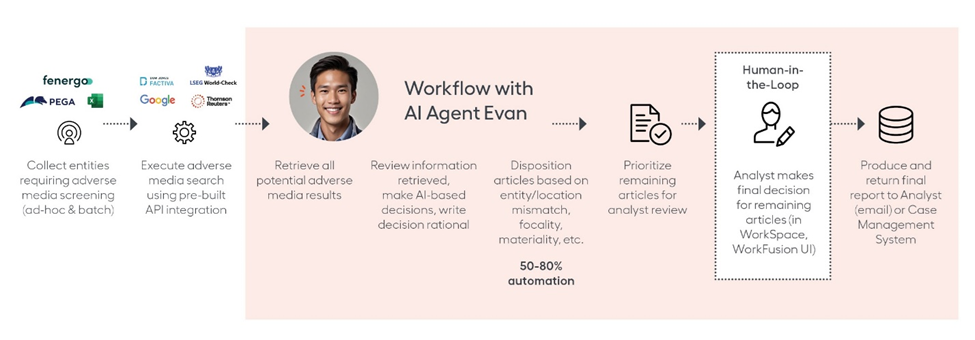
Notice that the AI Agent does not replace your existing system, and instead, works alongside to optimize it. Here (above), AI Agent Evan operates by taking information from a standard adverse media screening tool and reviewing it to prioritize news articles and other information about your customers and potential customers. Evaluating relevance, demographic data, level of material significance, and other attributes, Evan is prebuilt with deep industry and prior FinCrime knowledge to fully investigate an entity (persons or organizations) with as little information as just a name. He highlights articles/information that indicate risk, passing those cases to a human analyst to review. Whenever Evan makes a decision, he provides detailed justification in written, auditable form.
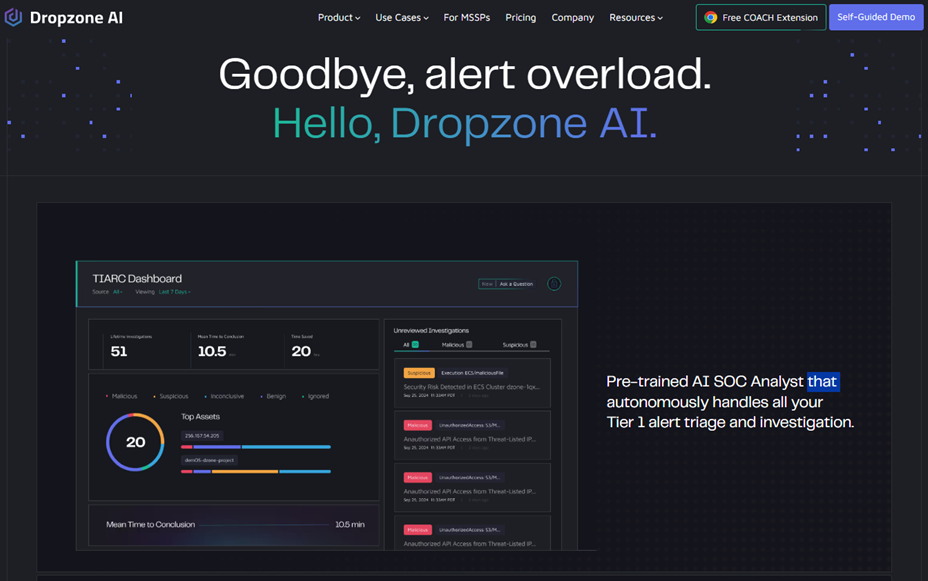
Do AI Agents designed for SOCs work the same way? To be clear, we at WorkFusion specialize in designing AI Agents for FCC operations. However, a cursory review of Agentic AI providers in the SOC space shows extreme similarities. For example, Dropzone AI’s homepage (https://www.dropzone.ai) describes their “Pre-trained AI SOC Analyst that autonomously handles all your Tier 1 alert triage and investigation.” Sounds familiar! And, as you can see from a screenshot, the value proposition is nearly identical (but focused on security, not FinCrime):
Industry leading banks have already adopted AI Agents
At WorkFusion, we count among our customers 4 of the top 5 U.S. banks (9 of the top 20), and our customers are having great success. Our AI Agents are resolving one million alerts per day. As for SOC AI Agents, once again we cannot speak for them, but the trajectory seems clear – AI Agents finally can deliver on the efficiency and efficacy gains of AI for various areas of bank operations.
To learn more, request a demonstration today.